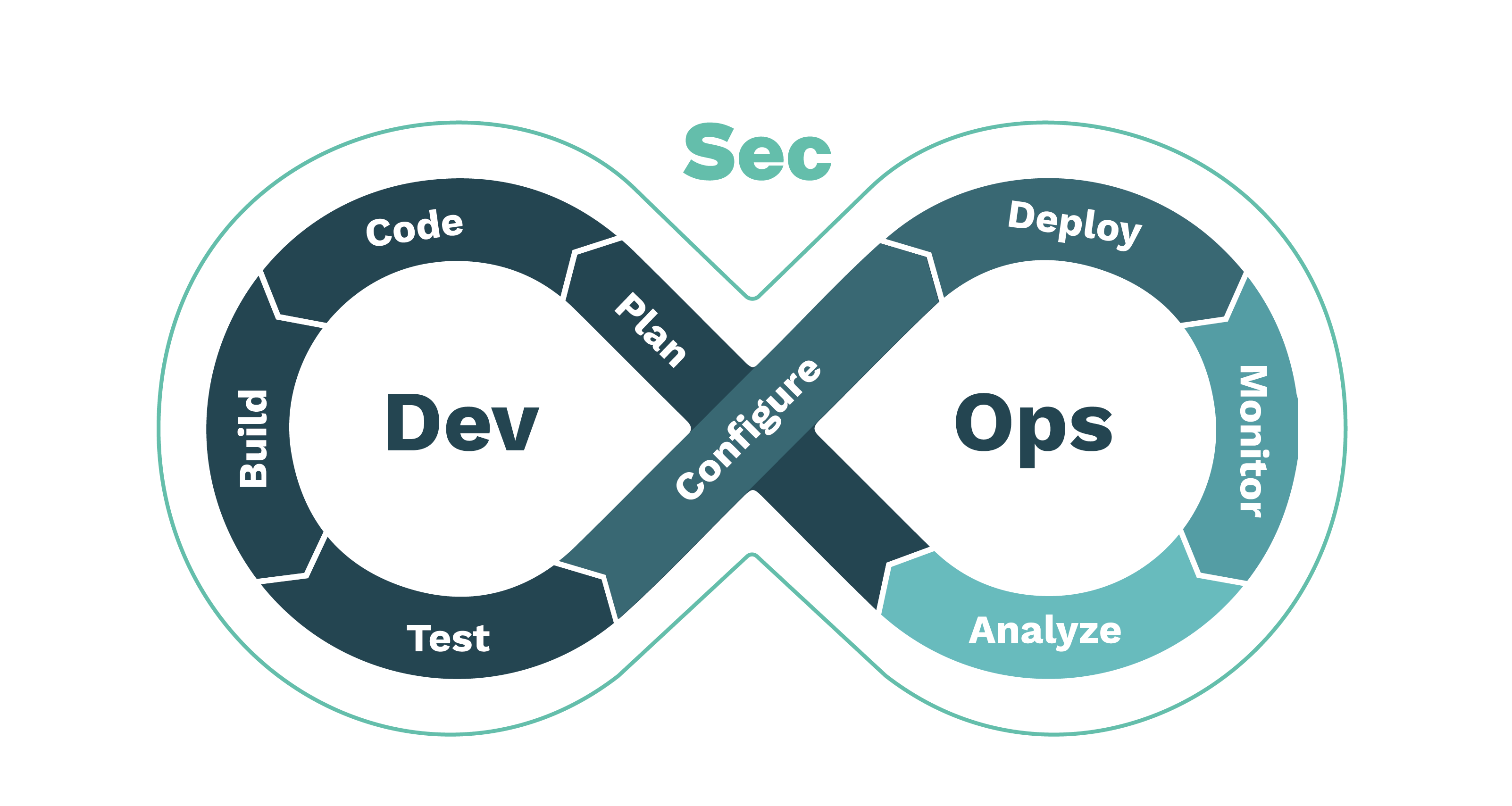
DevSecOps is a methodology that combines development, operations, and security practices to create a secure and efficient software development process. This guide is designed to provide beginners with an overview of DevSecOps principles and practical steps to implement it effectively.
- Understand DevSecOps Principles:
- Shift Left: Embrace a proactive approach by integrating security practices early in the development process.
- Automation: Leverage automation tools and processes to streamline security testing and deployment.
- Collaboration: Foster cross-functional collaboration and shared responsibility between development, operations, and security teams.
- Continuous Improvement: Continuously assess and enhance security practices to address emerging threats and vulnerabilities.
- Establish a Security Culture:
- Promote Security Awareness: Educate team members about common security risks, best practices, and the importance of secure coding.
- Encourage Responsibility: Instill a shared responsibility mindset where everyone understands their role in maintaining security.
- Integrate Security Practices:
- Secure Coding: Train developers in secure coding practices, such as input validation, parameterized queries, and proper error handling.
- Code Analysis: Utilize static code analysis tools to identify vulnerabilities and enforce coding standards.
- Automated Testing: Incorporate security tests, including vulnerability scanning, penetration testing, and security code review, into your CI/CD pipeline.
- Automate Security Processes:
- Infrastructure as Code: Use tools like Terraform or Ansible to define and manage infrastructure securely.
- Configuration Management: Automate configuration management processes to ensure consistency and security across environments.
- Continuous Monitoring: Implement automated monitoring and logging to detect and respond to security incidents promptly.
- Implement Secure Deployment:
- Immutable Infrastructure: Deploy immutable infrastructure, where components are not modified after deployment, reducing the risk of unauthorized changes.
- Containerization and Orchestration: Use containerization platforms like Docker and orchestration tools like Kubernetes to isolate applications securely.
- Embrace Security Testing:
- Dynamic Application Security Testing (DAST): Conduct DAST to identify vulnerabilities in running applications by simulating real-world attacks.
- Static Application Security Testing (SAST): Use SAST tools to analyze source code and detect security flaws early in the development process.
- Interactive Application Security Testing (IAST): Employ IAST tools to analyze running applications in real-time for security vulnerabilities.
- Continuous Monitoring and Incident Response:
- Real-Time Monitoring: Implement automated monitoring and alerting systems to identify and respond to security incidents promptly.
- Incident Response: Develop an incident response plan and regularly practice incident response exercises to ensure a coordinated and effective response.
Conclusion: DevSecOps is a transformative approach that brings together development, operations, and security to create a secure and efficient software development lifecycle. By embracing a proactive security mindset, leveraging automation, and fostering collaboration, organizations can build resilient and secure applications. Start by implementing the principles outlined in this guide, and continuously improve your security practices to stay ahead in the ever-evolving threat landscape.