Bagaimana OWASP Top Ten dapat membantu Seorang DevSecOps
The OWASP Top Ten is a widely recognized and respected list of the top ten most critical web application security risks. It is published by the Open Web Application Security Project (OWASP), a nonprofit organization focused on improving software security. The list is updated periodically to reflect the current threat landscape and to raise awareness about the most common and severe security vulnerabilities affecting web applications.
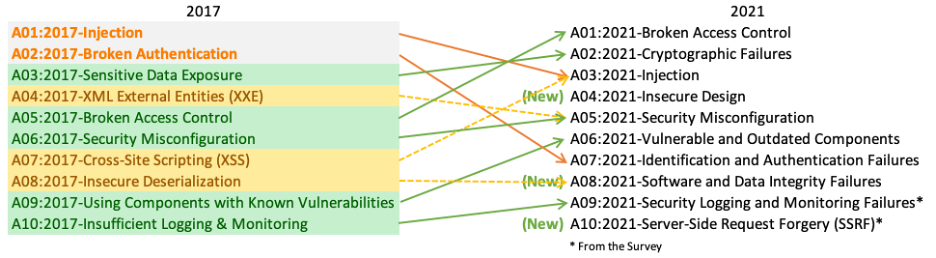
OWASP Top Ten list includes the following vulnerabilities:
-
Injection: This refers to security flaws that allow untrusted data, such as user input or external content, to be interpreted and executed as code. Common types include SQL injection and NoSQL injection.
-
Broken Authentication: When authentication and session management mechanisms are implemented incorrectly, attackers can compromise user accounts, gain unauthorized access, and impersonate legitimate users.
-
Sensitive Data Exposure: This occurs when sensitive data, such as passwords, financial information, or personal identifiable information (PII), is not adequately protected and can be accessed or stolen by unauthorized individuals.
-
XML External Entities (XXE): XXE vulnerabilities allow attackers to manipulate XML input, leading to disclosure of sensitive information, denial of service, and server-side request forgery.
-
Broken Access Control: Poorly enforced access controls can allow attackers to access unauthorized functionality or sensitive data.
-
Security Misconfiguration: When security settings are not properly configured, it can create opportunities for attackers to exploit vulnerabilities and gain unauthorized access.
-
Cross-Site Scripting (XSS): XSS allows attackers to inject malicious scripts into web pages viewed by other users, potentially leading to the theft of session cookies, account hijacking, or the spread of malware.
-
Insecure Deserialization: Deserialization flaws can allow attackers to execute arbitrary code or perform other malicious activities when an application processes serialized data from untrusted sources.
-
Using Components with Known Vulnerabilities: Integrating third-party libraries or components with known security vulnerabilities can expose an application to various attacks.
-
Insufficient Logging and Monitoring: Inadequate logging and monitoring can make it challenging to detect security incidents and respond to them in a timely manner.
It's important for developers, security professionals, and anyone involved in the software development lifecycle to be aware of these common vulnerabilities and take appropriate measures to mitigate the risks. The OWASP website (owasp.org) provides more in-depth information about each vulnerability on the Top Ten list, along with guidance on how to prevent and address these issues.
The OWASP Top Ten is an invaluable resource for beginners in the DevSecOps field as it provides a concise and prioritized list of the most critical web application security risks. Understanding and addressing these risks early in the development process is essential for building secure software. Here's how the OWASP Top Ten can help beginners in DevSecOps:
-
Security Awareness: The OWASP Top Ten introduces beginners to the most common security risks that web applications face. It raises awareness of potential vulnerabilities and helps developers and DevOps practitioners understand the importance of integrating security into the development process.
-
Prioritization: The list is prioritized, indicating the severity and prevalence of each vulnerability. Beginners can focus on addressing the high-priority risks first, ensuring that they are addressing the most critical security issues.
-
Guidance for Mitigation: Each item on the OWASP Top Ten comes with detailed explanations, examples, and guidance on how to mitigate the associated risks. Beginners can use these resources to learn about best practices and security measures to apply in their applications.
-
Educational Material: The OWASP Top Ten provides a wealth of educational material on various security topics. Beginners can delve into specific vulnerabilities, their impact, and ways to prevent them, helping them build a solid foundation in web application security.
-
Security Testing: Beginners can use the OWASP Top Ten as a reference to guide their security testing efforts. It helps identify what to look for during security assessments, such as code reviews, penetration testing, and vulnerability scanning.
-
Secure Coding Practices: By understanding the OWASP Top Ten, developers can adopt secure coding practices and apply them from the early stages of development. This proactive approach helps prevent security issues from being introduced into the codebase in the first place.
-
Integration into CI/CD Pipelines: DevSecOps is about integrating security into the continuous integration and continuous deployment (CI/CD) pipeline. The OWASP Top Ten provides a basis for implementing security checks and testing automation within the pipeline.
-
Collaboration and Communication: The OWASP Top Ten can serve as a common language between developers, security teams, and operations personnel. It facilitates better collaboration and communication when discussing security concerns and risk mitigation strategies.
-
Community Support: OWASP has a vibrant community of security professionals, developers, and enthusiasts. Beginners can take advantage of this community to seek advice, share knowledge, and participate in security-related projects and events.
-
Compliance and Industry Standards: Many industry standards and compliance frameworks reference the OWASP Top Ten. By addressing these vulnerabilities, beginners can help their organizations meet specific security requirements.
Remember that security is an ongoing process, and the threat landscape evolves continuously. Beginners in DevSecOps should continually learn, stay updated with the latest security trends, and apply security measures appropriate to their projects and environments. By leveraging the OWASP Top Ten as a starting point, beginners can build a strong security foundation and contribute to developing more secure and resilient software.
Conclusion:
The main point is that the OWASP Top Ten is a valuable resource for beginners in the DevSecOps field. It provides a prioritized list of the most critical web application security risks, raising awareness and understanding of common vulnerabilities. The OWASP Top Ten offers guidance for mitigating these risks, educational material, and helps with security testing and secure coding practices. By using this resource, beginners can integrate security into the development process, collaborate effectively, and address security concerns in their applications. The conclusion emphasizes the significance of continuously learning and staying updated with evolving security trends to build a strong security foundation and develop more secure software.